- HubPages»
- Technology»
- Internet & the Web»
- Viruses, Spyware & Internet Security
AntiVirus, AntiSpyware And Firewall - Ladies' Guide To Computer Security Essentials
Have you heard any of the words above and wondered what do they really mean? No? Well, that's quite natural.
There are many more interesting things in the world than this so I don't blame you at all. Unfortunately we live in such a reality that we need to have at least a rough idea what is this all about.
You may question if you really need to know any details, because you might think it's not a big deal.
Lack of online security
Your computer, laptop, iPad or even a mobile phone are your doors to the internet if they are connected. They give you the access to the virtual world in the same way as the big front door gives the access to your house.
Would you leave your doors unlocked knowing that there are many thieves in the neighbourhood? Even more, would you put a huge banner on your house saying „My doors are open, you can get inside easily”? I honestly doubt.
And this is exactly what you are doing when you connect your computer to the internet without any protection. In fact there are three main different entries that can let thieves into your computer and each of them needs to be protected. There is one type of a lock for each entry, and of course there are many companies that produce those locks.

AntiVirus software
So you've got the AntiVirus software that locks the main door. This is the one that keeps away thugs that want to destroy furniture or spray nasty things on your walls. Sometimes they are harmless as spraying can be easily removed. On other occasion however, they may put the whole house on fire so you could lose everything.
AntiSpyware or AntiMalware software
There is also AntiSpyware software that locks your backdoor so the spies cannot look into your cabinets and see what you have for dinner or steal your favourite jewellery along with credit cards.
They are usually harder to spot than viruses, but often more dangerous as they are phishing on the information. This group of thieves in the real world would search through your bank statements or install a bug in your telephone line and listen to your conversations. It’s not nice, is it?
Firewall - is essential as the bricks for the real wall
And the last one we talk about here is Firewall software that locks all your windows and other mouse holes you might have in your house. It keeps away thieves mainly looking for ways into your house so the other two groups we talked about, could get in and do their nasty job.
They are like small bugs trying all different places until they find the gap in your house structure and the way in. The moment they find it, they make it bigger until the thieves from other groups manage to get inside.
The real vs virtual world protection
In the real world you would not only lock the doors and windows to avoid burglary, but you would take a house content insurance to cover potential losses. You wouldn't leave the door unlocked if you knew you were living in a bad neighbourhood.
The same is true for the online reality, locking is a necessity. Unfortunately you cannot be certain you are completely secure. Same as with your house - someone may break in even with everything perfectly locked.
So you need to take care of protecting your content and your identity to cut the potential losses.
Fingers crossed no one breaks into my computer.
You may hope nothing will happen but what if?
If you will be attacked by the virus, your computer data might be completely wiped out. Are you prepared to lose all photos from years of travelling? Are you ready to lose your dissertation document or annual report for work you do?
If the answer is no, then you may add an additional thing to your computer security to do list - data backup. It’s nothing more than making a copy of your important data in the computer and storing it in a safe place.
Keylogger - the worst nightmare
What if the spy will break in but instead of happily destroying your data, it will start collecting them? How would you feel knowing that someone knows every username and password you are using, details to login to your bank account along with everything you have written in your emails?
You might not believe that anyone can do this but this is not a person, it’s a specially designed program. It goes under the name: keylogger. It knows everything you do on your computer, every click, every mouse move, every letter you type and all is sent to its master. Luckily, if you keep your computer protected it’s unlikely it gets in, unless you are a special target. Once it’s there, it still can be spot and removed.
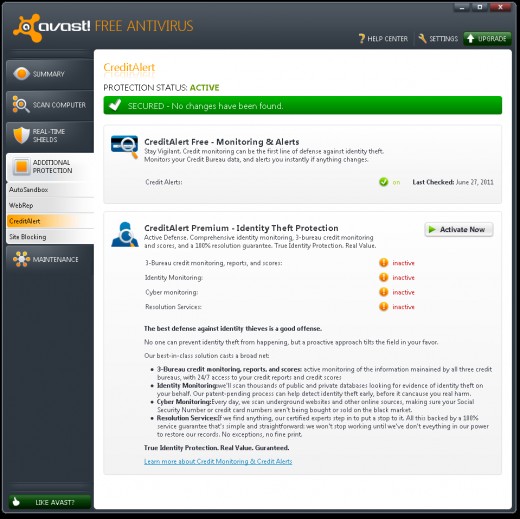
Regular security scans
Apart from locking your doors, windows and mouse holes, security protection software has one more job to do. It runs the scan of your computer data to check for any suspicious files.
It’s like having a SWAT team at your fingertips to check all the corners in every room of your house for potential criminals, so you can be sure it’s safe. The key is to scan your computer on regular basis so even if thieves get in, they won’t stay long.
What if the worst have happened?
Even with a full protection you may actually get into trouble. A virus, trojan or other malware program will get through. If you are lucky your scans will find out about it quite quickly and the damaged will be limited.
Still it might be too late and some critical data might be intercepted - your credit cards details or identity stolen. It may cause even more damage than if it happened in the real world as it’s hard to track down, so your best shot is to insure yourself against such an event.
You can take out the identity theft protection insurance. It usually comes with some additional elements like an option to register your documents details and credit cards numbers in a special system that alerts you whenever they are used by someone else.
How to install security protection software
I hope you will agree with me now that it’s necessary to have the protection for your computer. The trick is how to go about doing it. As I don’t know your level of experience with technology, I will suggest different ways of approaching the problem.
I. Technology and I don't get along very well
If you belong to the group that doesn’t really know much about techie stuff, either because it’s boring or because it's scary and you prefer to leave it to your partner then:
- You are absolutely right - make him to do the job. There is no reason you would need to know all the details as long as it runs as it should. So talk to your boyfriend.
- You need to be sure that he knows enough about this stuff so you can leave it to him. You may try to test his knowledge with any of the keywords here like casually asking him where the backup of your last photos is or what antivirus software he is using. If the answer starts with techie bubble than you know all is in good hands
- If the answer is “what???”, then you may need to look for an alternative. Think if you know any friend who is spending more time at the computer than sleeping and you’ve got your man. Alternatively you can look up yellow pages or ask friends to recommend you someone who knows this stuff.
- Ensure your partner knows how to maintain all the software that is installed, upgrades, scans, etc. and poke him from time to time with a question using any of the keywords from this hub to make him more vigilant.
- Next time you upgrade your bank account check if there is identity theft protection and consider investing the money. Now you can relax knowing that all was handled.
II. I've heard of the antivirus software before but don't know the details
If you heard of some stuff and have only vague idea about it but you would actually like to know more and be independent, then there is a starting point for you.
- If you use Windows, the firewall will be installed for you so you can ignore it for now. You need an antivirus and antispyware software ASAP, so you better get one first before researching the web. If you are brave enough to do it yourself I would suggest to start with free Avast antivirus and either Windows Defender or MalwareBytes antispyware.
- If you are afraid of installing it yourself, see points above about partner or friend doing the job for you. If they are not too geeky you may try and learn the process while they do it. You also may ask them questions about configurations and running scans so you will know how to maintain it yourself.
- Set up automatic scans - every night would be the best and ensure you always have the latest updates and virus databases.
- Once you’ve got it all setup, you just keep an eye on your computer - if you use it frequently you should easily spot anything unusual. Sometimes there are weird popups showing, or antivirus says that it found something but nothing is there or unexpected crashes keeps happening. All those signals are important and you need to react - run boot time scan for your machine. It’s the one that checks the data even before Windows system is loaded.
- Expand your knowledge - use the internet to learn more about available software and what is important about it. Articles comparing two or more packages together are the best as they often come with comparison of most important elements and a glossary to explain what they mean.
III. I have been fixing my computer way before I went to school
If you are in this group and the technology have no secrets for you, than you know already what to do. I bet you know much more than I do about the topic but I still have a couple of suggestions.
- Look around, your best friend might not be that lucky and probably needs help setting all up. She may be single or maybe her partner is a “what??” type so give her a helping hand.
- Write a hub about each aspect in more details for all of us who would love to know more but need someone to explain it in an easy way.
Things can be hard to see when they are too close
We have focused on keeping your computer safe in the global network and this is the place the danger will most likely come from. However, don’t overlook something that is really close.
Even if your computer is fully protected but you are in the same local network as another computer with open access, then the user of that machine can easily infect your system without any of you realising that. So please ensure all the computers, netbooks, laptops, etc. in your home network have similar level of security.


![Kaspersky Internet Security 2011 3-User [Old Version]](https://m.media-amazon.com/images/I/51DghVFbLuL._SL160_.jpg)




![How to Remove Kaspersky Password Protection? [Easily Recover] How to Remove Kaspersky Password Protection? [Easily Recover]](https://images.saymedia-content.com/.image/t_share/MTc2Mjk3NDcwOTAzNTkyMTI2/how-to-remove-kaspersky-password-protected-easily-recover.png)


